A security operation center (SOC) managed by a c-Community should be established and run according to cybersecurity industry best practices. It should specify the operating conditions for people, processes and technology. And, it should be geared for a holistic computer network defense (CND) approach. It should also have a tiered organizational structure with Tier 1 analysts on the front line managing the most fundamental and routine issues, Tier 2 analysts serving as gateways for triage, and Tier 3 analysts functioning in highly specialized fields. A step-by-step roadmap for the design and deployment of a SOC was developed by Torres in 2015 in a SANS Institute White Paper.
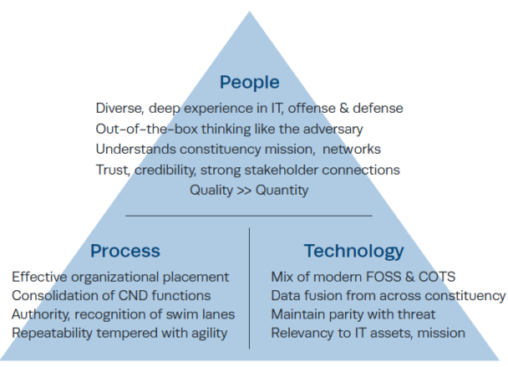
An important set of recommendations were published by the Mitre Corporation in 2014 (Zimmerman). These strategies can form the basis of a world-class c-Community SOC. Below are links to training materials for each of these strategies.
Ten Strategies of a World-Class Cybersecurity SOC
S1 – Consolidate Computer Network Defense Under One Organization
S2 – Achieve Balance Between Size & Agility
S3 – Give the SOC the Authority to Do Its Job
S4 – Do a Few Things Well
S5 – Favor Staff Quality Over Quantity
S6 – Maximize the Value of Technology Purchases
S7 – Exercise Discrimination in the Data You Gather
S8 – Protect the SOC Mission
S9 – Be Sophisticated Consumer of Cyber Threat Intelligence
S10 – Stop. Think. Respond…. Calmly
The reader is encouraged to reference the original report for full details.
View our online, interactive course!
_________________________________
References:
Torres, A. (2015, May). Building a World Class Security Operations Center: A Roadmap. A SANS Institute White Paper.
Zimmerman, C. (2014). Ten Strategies of a World-Class Cybersecurity Operations Center. The Mitre Corporation.
